Last Tuesday, your head of AI asked for an environment to test a new LLM integration with customer data.
You said it would take three weeks to provision something secure.
She nodded. Then she spun up an AWS account using her personal credit card.
You probably don’t know about it yet. You will during the next audit.
This isn’t a story about shadow IT.
It’s a story about what happens when infrastructure can’t keep up with strategy.
The CEO Wants an Answer by Friday
Here’s a conversation that happened somewhere in your organization last month:
CEO: “Can we use AI to analyze the due diligence data from the acquisition target?”
You: “Yes, but we need to provision a secure environment first. Should have it ready in…”
CEO: “The board meeting is Friday. We need this now.”
You: “We can fast-track it, but it won’t have all the proper controls…”
CEO: “Do what you need to do. Just get it done.”
What you said: “I’ll make it work.”
What you meant: “I’m about to grant an exception I’ll regret in six months.”
What happened: You probably used a shared cloud account with elevated permissions, told yourself it was “just this once,” and moved on.
The work got done. The board was happy. And you added one more entry to the invisible ledger of technical debt that nobody tracks and everybody lives with.
The Innovation You’re Not Seeing
Your fraud investigation team wants to test a new detection model.
Your threat intel team needs to run OSINT on a potential state-sponsored actor.
Your product team wants to experiment with an AI agent that could automate customer support.
Every one of these initiatives starts with the same question: “Where do we run this?”
And every one of them ends with the same answer: “We’ll figure something out.”
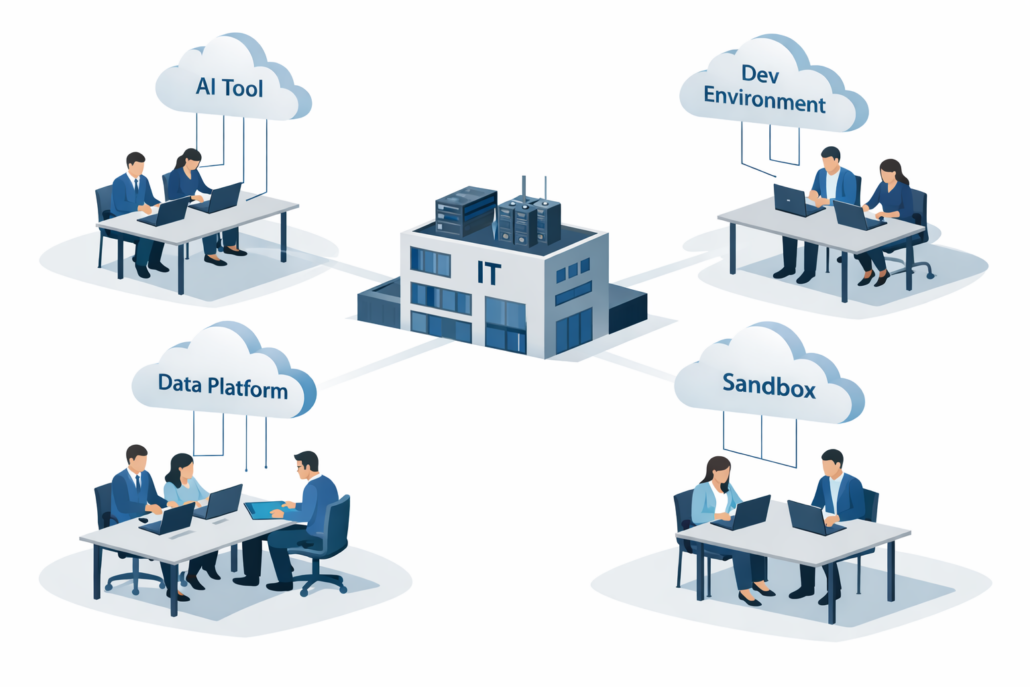
“Figure something out” means:
- Using production systems they shouldn’t touch
- Spinning up unmanaged cloud instances
- Working on personal devices
- Asking a consultant to “just handle it”
- Not doing the work at all
You know this is happening. You just don’t know how often.
The Conversation Your CISO Isn’t Having With You
Your CISO sees something you don’t.
She sees the work that almost happened.
- The M&A deal that took six months instead of three because you couldn’t analyze the target’s codebase safely
- The threat intelligence your team isn’t sharing with industry peers because there’s no secure way to exchange it without risking attribution
- The AI experiments your data science team abandoned because they couldn’t get access to realistic datasets without violating policy
She’s not telling you about these because there’s no ticket for “work that didn’t happen.”
There’s no incident report for “strategic initiative delayed due to infrastructure constraints.”
There’s no dashboard that shows “capability suppressed.”
(But she knows. And it’s keeping her up at night.)
Your Infrastructure Was Built for a Different Game
Ten years ago, high-risk digital work meant:
- Malware analysis in a dedicated lab
- Forensic investigation on isolated systems
- Penetration testing in carefully controlled environments
That world had clear boundaries. Known threats. Predictable workflows.
Your infrastructure was built for that world.
Today, high-risk digital work means:
- Testing AI agents that might hallucinate customer data
- Running strategic analysis on M&A targets in contested regulatory environments
- Experimenting with tools that could expose your corporate identity
- Collaborating with external researchers without leaking IP
Your infrastructure wasn’t built for this.
And retrofitting it isn’t working.
The Exception Economy
So you do what every other IT leader does.
You grant exceptions.
Formal ones, documented in change control tickets with “time-limited compensating controls.”
Informal ones, authorized over Slack with “just this once, but let’s be careful.”
Verbal ones, whispered after meetings with “I didn’t see anything, you didn’t tell me anything.”
The exceptions are how work gets done now.
They’re not the workaround. They’re the system.
What Happens When Infrastructure Becomes the Constraint
Your organization is making strategic decisions based on what infrastructure allows, not what strategy demands.
You’re not expanding into that new market because you can’t do the competitive analysis safely.
You’re not launching that AI feature because you can’t test it without risking compliance violations.
You’re not partnering with that external research group because you can’t share threat data without exposing your own infrastructure.
Infrastructure has quietly become the limiting factor for strategy.
And nobody’s talking about it in board meetings.
The CIO/CISO Paradox
You and your CISO are both right.

You say…
The work is getting done.
You measure delivery velocity.
You’re optimizing for speed.
She says…
It’s getting done unsafely.
She measures unmitigated risk.
She’s optimizing for control.
You both want to enable the business. But you’re doing it with infrastructure that forces you to choose between capability and security.
That’s not a people problem.
That’s not a policy problem.
That’s an infrastructure problem.
The Question Nobody’s Asking
What would your organization be capable of if infrastructure wasn’t the constraint?
If your AI team could spin up a secure environment in minutes, not weeks.
If your threat intel team could collaborate externally without exposure risk.
If your fraud investigators could test new models on production-like data without policy exceptions.
If your M&A team could analyze acquisition targets in real-time without waiting for IT to provision something.
How much faster could you move?
How many more strategic bets could you take?
How much suppressed capability would you unlock?
The Organizations That Win
The organizations that close this infrastructure gap won’t just be more secure.
They’ll be more capable.
More agile.
More strategic.
They’ll be able to say “yes” when their executives need to move fast on high-stakes initiatives.
They’ll be able to experiment with AI without waiting for three-week provisioning cycles.
They’ll be able to execute their strategy without choosing between speed and safety.
Meanwhile, the organizations still operating in the exception economy will keep improvising. Keep granting exceptions. Keep choosing between capability and control.
Keep wondering why their competitors are moving faster.
This Isn’t a Prediction. It’s Already Happening.
Somewhere in your organization right now, someone is spinning up an unofficial environment because they can’t wait for IT.
Somewhere, a strategic initiative is being delayed because there’s no safe place to run it.
Somewhere, your CISO is granting an exception she wishes she didn’t have to.
The infrastructure gap isn’t coming.
It’s here.
And it’s widening.

So What Do You Do?
You can keep managing the exception economy.
Keep improvising. Keep granting exceptions. Keep hoping nothing breaks before the next audit.
Or you can close the gap.
Build infrastructure that makes exceptions unnecessary.
Infrastructure that gives your teams secure, governed, on-demand environments for the high-stakes work that defines your competitive advantage.
Infrastructure that aligns what your CIO needs and what your CISO requires.
Infrastructure that turns security from a bottleneck into an accelerator.
The choice isn’t whether your organization will do high-risk digital work.
The choice is whether you’ll have infrastructure that supports it.
Or whether you’ll keep operating in the exception economy until something breaks.
What would you be capable of if infrastructure wasn’t the constraint?