Use Cases
Secure
Enclaves
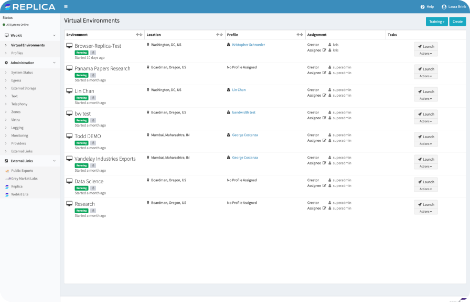
Effortlessly enable Secure Data Sharing with Patented Control
Replica is a simple yet robust solution that enables secure multi-party collaboration and privacy, while also hardening your enterprise infrastructure against attack. Designed for multi-national military collaboration, where complex treaties and laws dictate data access and permissions, Replica simplified the creation and management of secure enclaves to be accessible for all our customers.