Use Cases
Organizations conducting critical operations have long faced a difficult dilemma: traditional security approaches force choices between protection, access, and speed, compromising at least one. The Replica platform shatters this paradigm by providing complete isolation without operational friction. Our patented technology enables security teams, researchers, strategists, and developers to access sensitive sources, analyze threats, and collaborate across boundaries without exposing networks, revealing identity, or sacrificing agility. From corporate infrastructure to untrusted digital territories, Replica transforms how organizations approach high-stakes work.

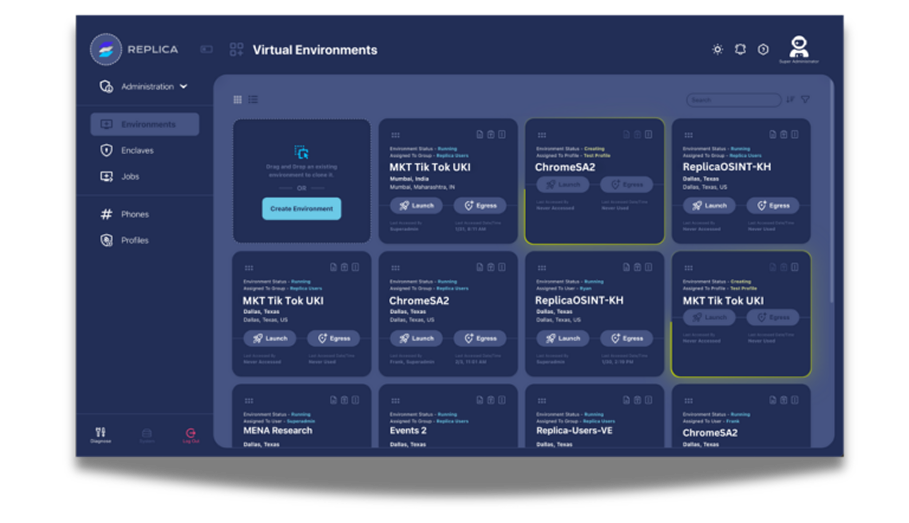
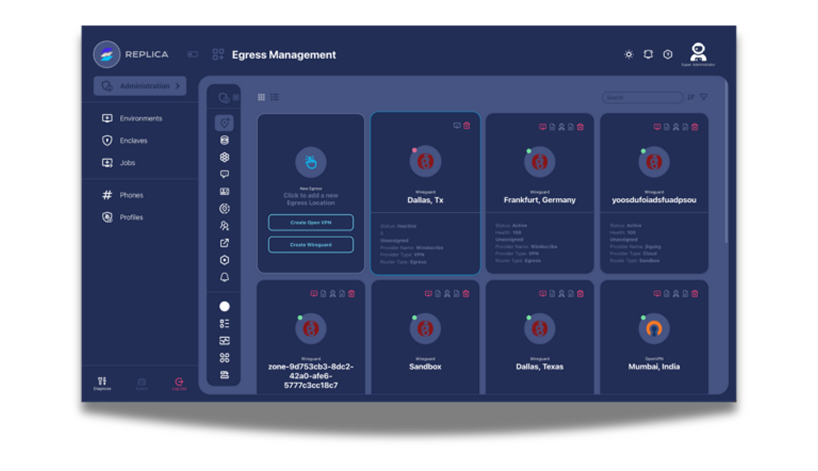
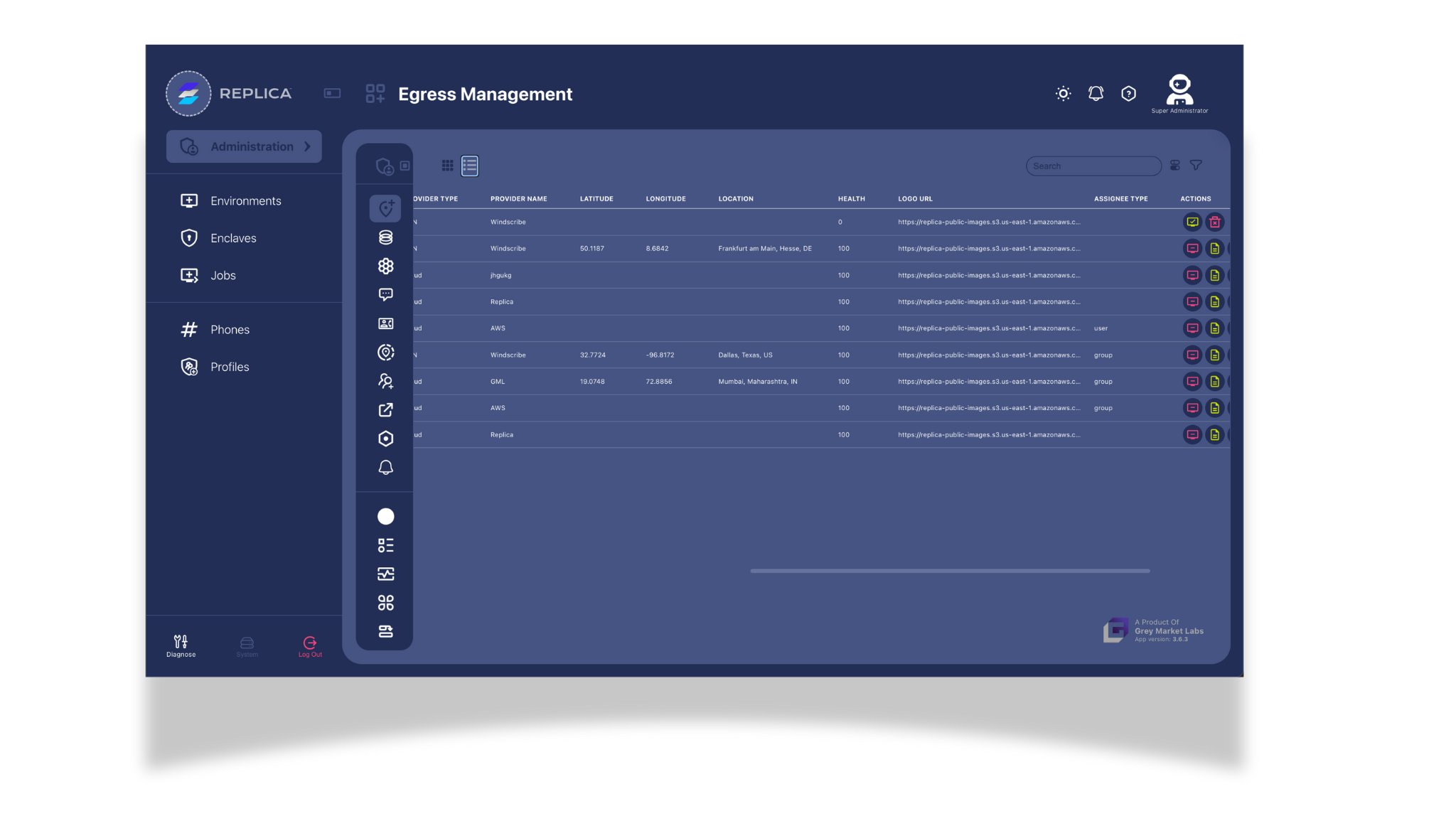
Eliminate IT bottlenecks with zero-touch deployment, instant activation, and seamless integration into existing workflows. Instantly scale from 5 to 10,000+ users.
Conduct high-stakes research, access restricted content, and execute threat analysis with complete anonymity and unattributable digital footprints.
Fast-track M&A, R&D, and strategic ventures with secure environments that enable rapid exploration and evaluation while maintaining complete privacy.
Streamline operations with automated data collection, scheduled intelligence gathering, and secure sharing.
The world’s first and most comprehensive secure environments platform, built to protect your most critical operations while enabling seamless execution.
