Digital Risk & Fraud
Financial institutions, healthcare providers, retail organizations, and government agencies face increasingly sophisticated fraud schemes targeting their customers and services. The Replica platform enables security teams to deploy anti-fraud honeypots, identify high-risk customer demographics, analyze specific attack methodologies, and safely examine malicious payloads without exposing corporate systems. Replica's patented zero-trust architecture ensures fraud investigators can gather actionable intelligence on criminal tactics while maintaining complete protection of networks, data, and personnel.
Access criminal forums, messaging platforms, and dark web marketplaces securely. Maintain anonymous digital identities that prevent attribution to your organization, document all investigative activities with audit trails, and collaborate securely with internal teams and law enforcement partners.
Create isolated environments where payment system testing and fraud analysis can occur safely. Evaluate transaction scenarios without exposing production infrastructure, use specialized tools within the secure environment to examine fraud patterns, and maintain regulatory compliance.
Schedule recurring collections from fraud-related data sources. Automate monitoring of criminal forums, marketplaces, and communication channels, establish persistent collection capabilities with rotated attribution, and aggregate data securely for comprehensive pattern analysis.
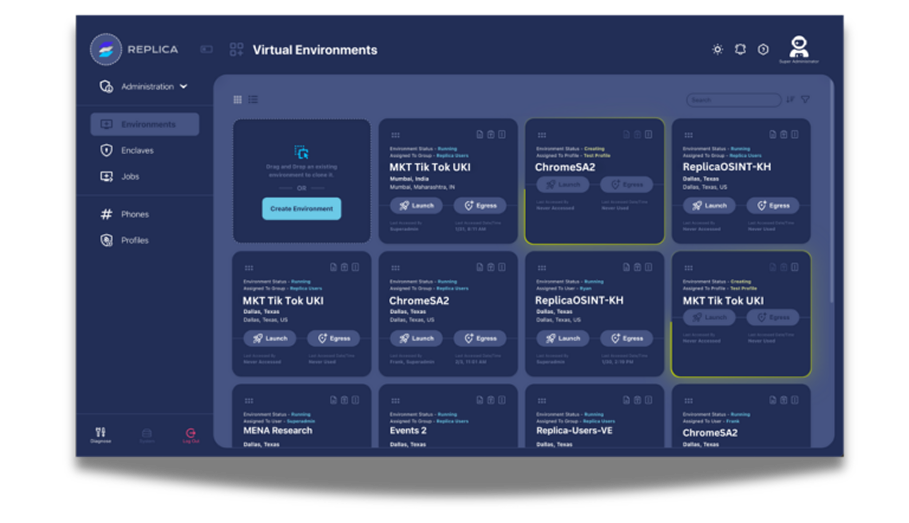
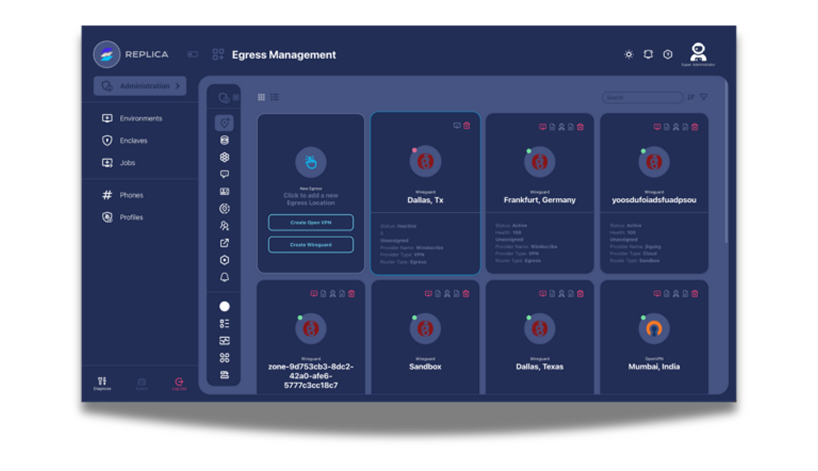
Recreate fraud techniques in isolated environments. Analyze social engineering approaches and technical exploitation methods, document complex fraud methodologies, and develop countermeasures without exposing defensive strategies.
Monitor marketplaces, social media, and websites for brand infringement. Investigate counterfeit operations without revealing corporate identity, document brand abuse with evidence collection and coordinate with legal teams and law enforcement for takedowns.
Access criminal platforms without attribution
Maintain comprehensive audit trails for legal proceedings
Conduct detailed analysis without exposing production networks
Schedule recurring monitoring of fraud sources
Investigate counterfeit operations without revealing identity
Evaluate payment systems without exposing production networks