Technology Evaluation & Isolation
Organizations face significant challenges evaluating and integrating third-party technology without exposing corporate systems to potential security risks. The Replica platform enables teams to safely evaluate, isolate, and operate technology without compromising corporate networks or intellectual property.
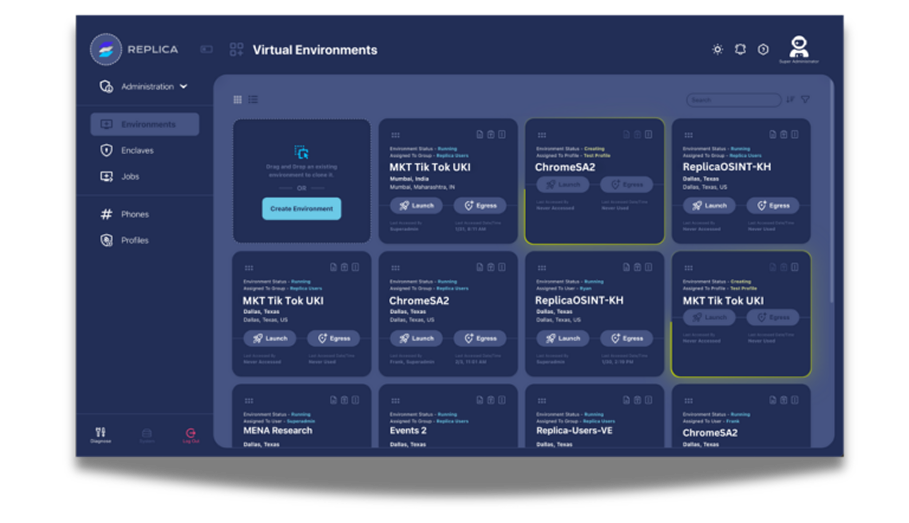
Create isolated environments for testing third-party applications. Analyze software behavior without exposing corporate networks, evaluate security and compliance implications before deployment.
Isolate legacy applications in secure environments separated from modern systems. Enable continued operation without exposing corporate networks to outdated security, provide modern access methods to legacy functionality, and maintain compliance with security policies despite legacy technology.
Create isolated environments specifically designed for high-risk code execution and evaluation. Run potentially dangerous code with complete separation from corporate networks, maintain configurable audit capabilities, prevent data exfiltration through patented security controls, and enable essential functionality without compromising security.
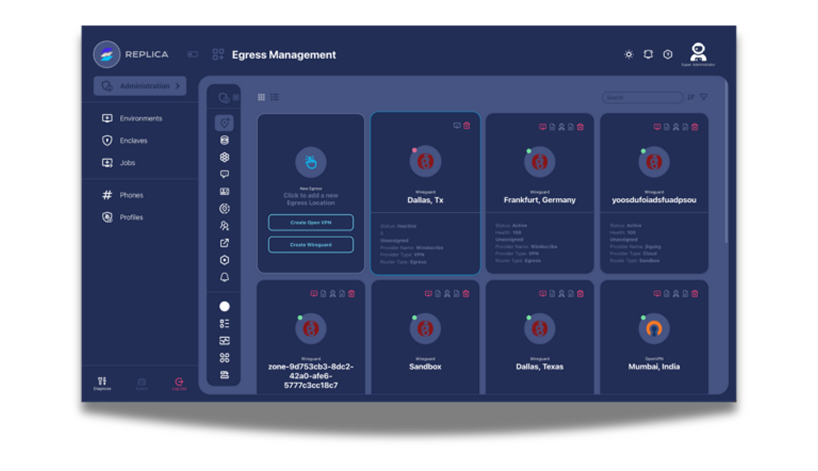
Verify vendor security claims in fully separated testing spaces. Evaluate security controls and data protection capabilities, document findings with detailed technical analysis, and assess compliance implications before implementation.
Establish secure testbeds for cutting-edge technologies like AI, IoT, and blockchain. Validate integration approaches without risk, assess security and compliance implications of emerging solutions, and document findings for strategic technology planning.
Test third-party applications without exposure
Isolate outdated systems securely
Operate necessary but risky code safely
Verify security claims without corporate risk
Test external APIs without compromising systems
Isolated environments for experimental coding
Replica provides complete isolation that prevents security risks during technology evaluation. The platform creates secure, contained environments where you can safely test unknown applications without exposing your organization's infrastructure. This accelerates your evaluation process while maintaining strict separation between untrusted technology and your production systems.