Intelligence & Research
Organizations conducting high-stakes intelligence and research operations struggle to balance critical access, security, and operational speed. The Replica platform enables professionals to access difficult to reach sources without attribution, collect vital intelligence securely, and collaborate without compromising operations.
Conduct research across social media, news sources, and public records while maintaining anonymity. Create multiple isolated digital personas with realistic footprints, maintain audit trails, and collaborate securely without exposing methodologies.
Securely access Tor, I2P, and specialized networks without exposing corporate infrastructure. Maintain realistic personas across closed forums, isolate potential threats, and collect intelligence with comprehensive logging and chain of custody controls.
Monitor adversary infrastructure, forums, and communication channels securely. Automate intelligence collection with scheduled tasks, analyze potential threats in isolated environments, and share intelligence across security teams with detailed provenance.
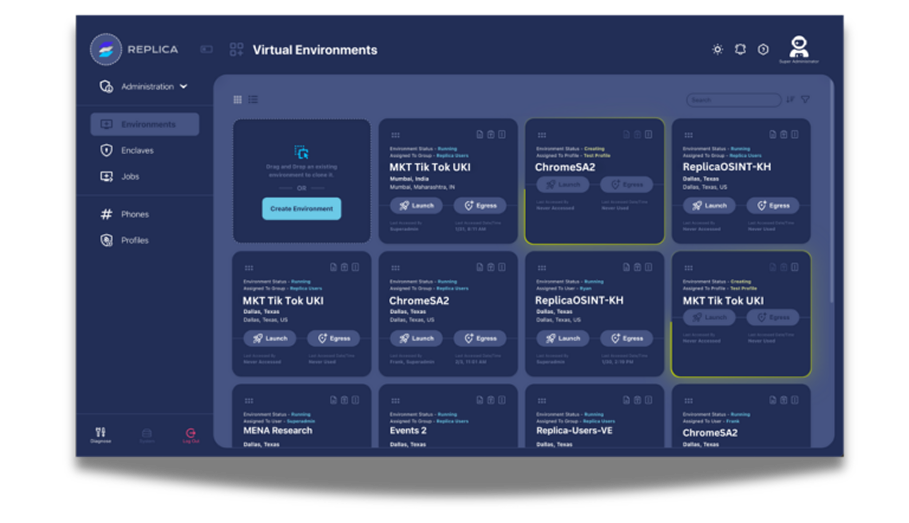
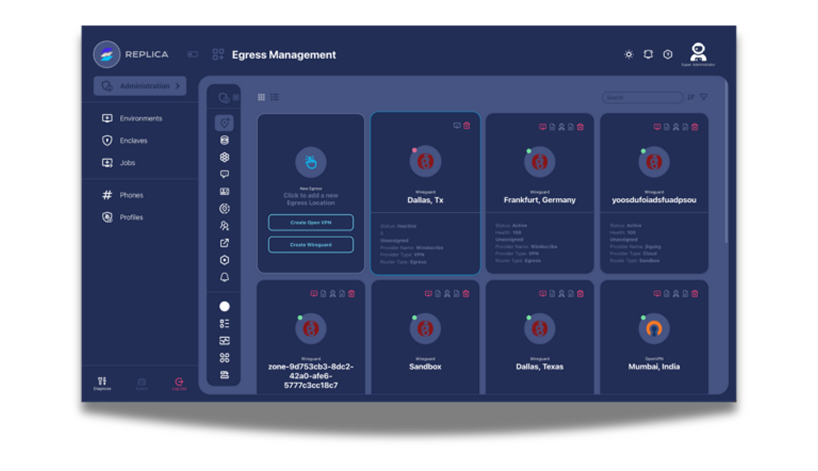
Test exploit code and vulnerability techniques in completely isolated environments. Analyze suspicious code without risk to systems, document findings with comprehensive audit trails, and collaborate securely while maintaining confidentiality.
Create consistent digital personas for long-term operations, communicate through isolated channels that prevent attribution, document all activities with comprehensive logging, and protect operational security through complete isolation.
Navigate with realistic, region-specific footprints that adapt to any environment
Complete separation of all systems, data, and networks from corporate infrastructure
Launch protected environments in seconds for immediate mission execution
Track every action with comprehensive logging while maintaining operational security
Securely share intelligence and work together without risk of exposure
Safely collect from geo-blocked, mobile-only, and closed platforms
Choose Replica when your operations demand both uncompromising security and unrestricted access. The platform delivers military-grade protection without sacrificing operational agility. Replica eliminates traditional trade-offs, enabling your teams to safely access any source, collaborate privately, and advance critical work 10x faster while maintaining complete organizational control and compliance.