Cybercrime Prevention & Analysis
Replica's full computing environments enable cybersecurity teams to safely combat sophisticated threats through complete isolation. Security teams can securely transfer suspicious content between assessment, triage, and analysis stages, safely detonate and forensically examine malicious code without risking corporate networks, while maintaining full auditability throughout. Even the most dangerous cyber threats can be thoroughly analyzed while keeping systems, networks, and data completely protected.
Detonate and analyze malware in completely isolated, disposable environments. Observe malware behavior with full system visibility, extract indicators of compromise without risking production systems, and securely share samples and analysis results with team members and trusted partners.
Deploy realistic decoy systems that mimic production environments. Monitor adversary activities with comprehensive logging, isolate deception environments from operational networks, and gather detailed intelligence on adversary tactics and techniques.
Examine potentially compromised systems with complete observability. Document all forensic activities with detailed logging and recording, preserve evidence in secure storage, and enable team-based investigation with secure collaboration tools.
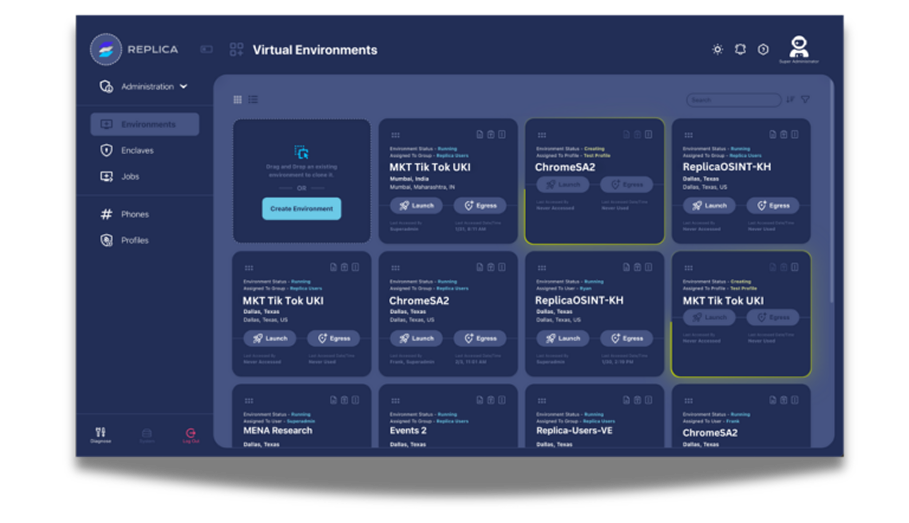
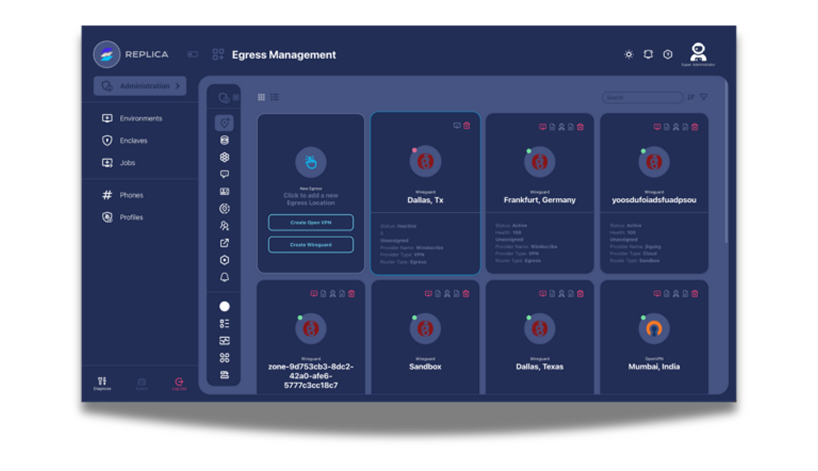
Recreate attack sequences that mimic production systems. Test defensive controls against reconstructed techniques, document methodologies with comprehensive logging, and share findings securely across teams.
Conduct realistic attack simulations in isolated environments without operational risk. Test security controls and detection capabilities, document findings with comprehensive evidence collection, and collaborate securely between red and blue teams during purple team exercises.
Analyze malicious code in fully separated environments
Safely engage threat actors with complete anonymity
Eliminate post-analysis cleanup requirements
Maintain detailed documentation for all security activities
Share findings safely across security functions
Streamline repetitive security processes
Replica delivers full isolation for all cybersecurity operations, malware analysis, forensic investigation, attack simulation, and adversary deception. Our environments eliminate risk to production systems while enabling complete visibility and seamless team collaboration. Investigate threats, test defenses, and reconstruct attacks with both protection and efficiency.