Traditional security forces impossible trade-offs between access, speed, and protection. Replica eliminates these constraints with secure digital environments that enable teams to operate without compromise.
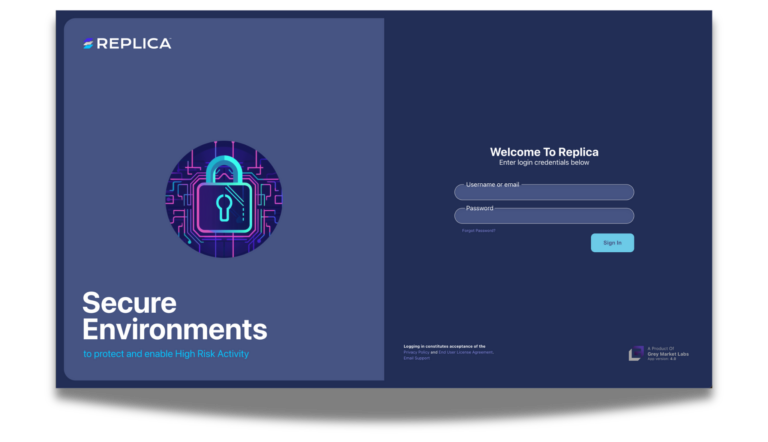
Eliminate IT bottlenecks with zero-touch deployment, instant activation, and seamless integration into existing workflows. Instantly scale from 5 to 10,000+ users.
Conduct high-stakes research, access restricted content, and execute threat analysis with complete anonymity and unattributable digital footprints.
Fast-track M&A, R&D, and strategic ventures with secure environments that enable rapid exploration and evaluation while maintaining complete privacy.
Streamline operations with automated data collection, scheduled intelligence gathering, and secure sharing.
Work in fully isolated, controlled environments with managed attribution and realistic digital footprints.
Safely access geo-blocked, mobile-only, and closed intelligence sources.
Enable secure teamwork on sensitive projects with built-in compliance, training, and audit-ready controls.
Streamline operations with automated data collection, scheduled intelligence gathering, and secure sharing.
Kubernetes orchestration automates manual processes and secures interactions between containers.
Deploy Replica as a SaaS model or managed service across cloud, on-prem, hybrid, or portable edge devices.
Overcome limitations of browser isolation and remote access solutions for secure, real-time collaboration on sensitive communications.
Integrate with IdAM, encryption, storage, cross-domain, audio and video, reporting, and alerting tools.
Leverage session recordings, network logging, user activity history, and system monitoring for compliance and audit readiness.
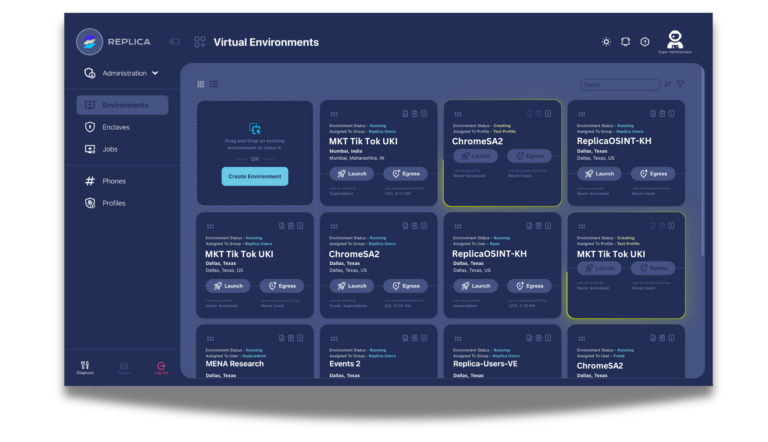
Investigate threats across any platform anonymously – from mobile to restricted sources to closed forums. Automate collection and analyze safely without exposure.
Uncover fraud and illicit activities by accessing hard-to-reach data worldwide. Gather evidence while maintaining compliance.
Isolate, detonate, and reverse-engineer malware and adversary infrastructure in a fully contained, disposable environment, without risking corporate networks or endpoints.
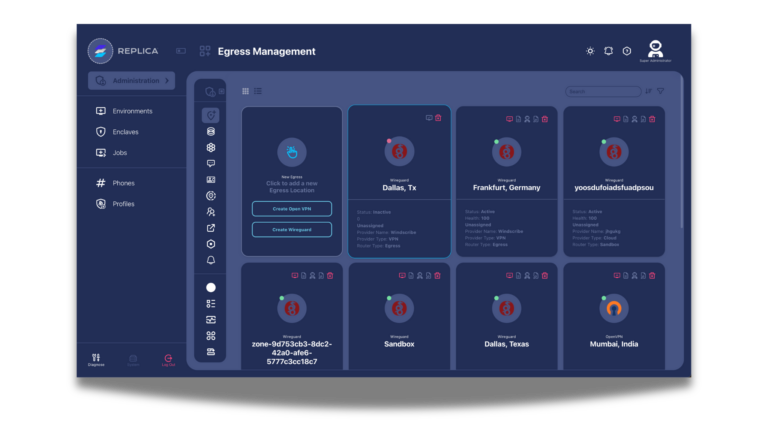
Access and analyze content across dark web sources, closed forums, and restricted platforms while maintaining complete anonymity and chain of custody.
Research acquisition targets and partnerships anonymously. Access market intelligence across restricted regions without revealing interest.
Quickly gain control and oversight of technology and operations from mergers and acquisitions, ensuring seamless integration and maximized value.
Replica’s patented technology isolates every layer, hardware, OS, applications, and networks, while maintaining realistic yet obfuscated digital footprints that adapt to global conditions. This ensures operational security, speed, and full compliance in high-risk environments.
The world’s first and most comprehensive secure environments platform, built to protect your most critical operations while enabling seamless execution.