The world's first zero-trust isolated environments platform. Enable unrestricted innovation and conduct high-stakes work without sacrificing speed for security. Deploy secure isolated labs and workspaces in seconds—protected by our patented anonymous attack surface, enterprise observability, and comprehensive data controls.


Legacy security architectures create friction and slow strategic initiatives. With 82 percent of breaches involving cloud assets and 75 percent of employees adopting unsanctioned tech, traditional perimeter-based approaches either leave you exposed or grind innovation to a halt.
Replica delivers full computing environments that empower organizations to conduct high-stakes work—securely and behind an anonymous attack surface. Our patented zero-trust isolated environments eliminate traditional trade-offs between security and speed.
Secure environments designed for innovation, mission-critical security, investigations, and operations.
Safely experiment with AI and test untrusted software, accelerate M&A workflows, enable secure third-party collaboration, and speed R&D innovation—all while protecting IP and maintaining compliance.
Uncover fraud and illicit activities by accessing hard-to-reach data worldwide. Gather evidence while maintaining compliance.
Access and analyze content across dark web sources, closed forums, and restricted platforms while maintaining complete anonymity and chain of custody.
Isolate, detonate, and reverse-engineer malware and adversary infrastructure in a fully contained, disposable environment, without risking corporate networks or endpoints.
Quickly gain control and oversight of technology and operations from mergers and acquisitions, ensuring seamless integration and maximized value.
Investigate threats across any platform anonymously – from mobile to restricted sources to closed forums. Automate collection and analyze safely without exposure.
Security without complexity. Operations without limits. Replica activates in seconds, eliminating IT bottlenecks and seamlessly integrating with existing security frameworks.

Replica enables high-stakes operations with uncompromising security, seamless collaboration, and full compliance, protecting critical assets while ensuring complete control.
Built to work with your existing tools.
Trusted by Industry Leaders to Power Secure Operations




19/09/2025
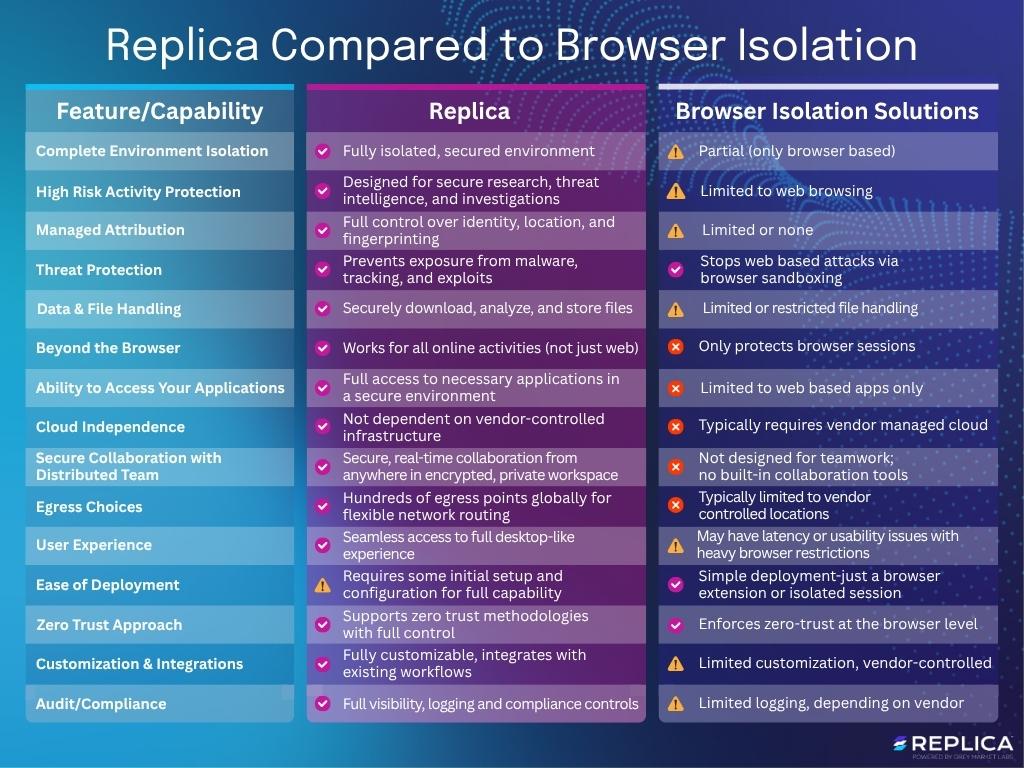
In today’s threat landscape, organizations conducting sensitive activities face a difficult choice: maintain rigorous security at the cost of operational agility or sacrifice protection for speed. Traditional browser isolation solutions emerged as a partial answer, but they fall short when teams need to conduct truly high stakes work like threat intelligence collection, malware analysis, fraud investigations, or M&A due diligence.
While browser isolation provides a valuable layer of protection for everyday web browsing, it simply wasn’t designed for the comprehensive security requirements of mission-critical activities. Organizations conducting high stakes work quickly hit browser isolation limits when they need unrestricted access, secure team collaboration, or comprehensive operational security.
The Browser Isolation Gap
Browser isolation solutions serve an important purpose: they protect against web-based threats by sandboxing browser sessions. However, this approach creates significant blind spots for organizations conducting high-stakes work:
Limited Scope of Protection: Browser isolation only secures web browsing activities, leaving gaps when teams need to use desktop applications, mobile interfaces, or specialized tools for intelligence collection and analysis.
Restricted Access: Many critical intelligence sources, dark web platforms, and geo-blocked resources actively detect and block traffic from known browser isolation services, limiting investigators’ ability to gather essential information.
Collaboration Challenges: Browser isolation wasn’t designed for secure teamwork. Teams conducting sensitive investigations need to share files, coordinate activities, and maintain full auditability, while preserving operational security.
Attribution Exposure: While browser isolation can mask some digital fingerprints, it typically doesn’t provide the comprehensive attribution management required for sensitive intelligence work or competitive research.

A Comprehensive Alternative: On-Demand, Secure Digital Environments
The Replica platform offers a fundamentally different approach. Rather than isolating just the browser, Replica creates complete, secure environments that enable teams to conduct any type of high stakes work without compromise.
Complete Environment Isolation: Unlike browser-only solutions, Replica provides fully isolated computing environments with zero-trust architecture across hardware, OS, applications, and network layers. This is essential for use cases like malware analysis, where analysts must interact with binaries, inspect registry activity, observe system modifications, and simulate real-world execution environments.
Managed Attribution: Built by cyber counterintelligence experts, Replica’s patented technology maintains realistic digital footprints that are adaptable based on global conditions. This enables access to restricted sources while maintaining complete anonymity.
Unrestricted Access: Replica environments can access geo-blocked content, mobile-only platforms, closed forums, and dark web sources that often block traditional browser isolation services. Intelligence teams can gather critical information from previously inaccessible sources.
Secure Collaboration: Purpose-built for teamwork, Replica enables secure, real-time collaboration through encrypted workspaces, secure file sharing via a proprietary system, with comprehensive audit trails.
Real-World Impact: From Limitations to Capabilities
The difference becomes clear when examining specific use cases:
Threat Intelligence Collection: Browser isolation might protect analysts while browsing known threat feeds, but it can’t provide access to closed forums, mobile-only platforms, or geo-restricted sources where critical intelligence often resides. Replica enables comprehensive collection across all these channels while maintaining complete anonymity.
Malware Analysis: Here is where browser isolation truly breaks down. While it can view webpages safely, it fails to offer the isolation depth required to inspect malware behavior. It does not enable access to system-level activities, nor does it have the ability to run or analyze binaries. Analysts cannot run tools like memory inspectors or packet sniffers—or safely download and execute malware samples for study. Replica, in contrast, provides dedicated sandboxed environments that enable full forensic analysis of unknown files, reverse engineering, and system interaction in a secure setting.
Fraud Investigations: Financial crime investigations often require accessing region-specific platforms, mobile applications, and social media channels that detect and block browser isolation services. Replica’s managed attribution enables investigators to access these resources naturally while maintaining operational security.
M&A Due Diligence: Competitive research demands access to restricted databases, regional platforms, and confidential sources. Browser isolation’s limited scope and detectable signatures can compromise research efforts, while Replica enables comprehensive market intelligence gathering without revealing corporate interest.
The Enterprise Security Evolution
Organizations conducting high stakes work need more than point solutions; they need platforms designed specifically for their unique requirements. Replica represents the evolution from reactive security tools to proactive enablement platforms.
Zero-Trust by Design: Built on true zero-trust architecture, Replica ensures complete isolation between secure environments and corporate infrastructure, eliminating lateral movement risks even during the most sensitive activities.
Instant Deployment: Unlike traditional security approaches that create IT bottlenecks, Replica environments deploy in minutes, enabling teams to begin critical work immediately rather than waiting days or weeks for security approvals.
Enterprise Control: While providing complete operational privacy, Replica maintains comprehensive audit capabilities, compliance controls, and granular access management that enterprise security teams require.
The Future of Secure Work
As threat landscapes evolve and regulatory requirements intensify, organizations need security solutions that enhance rather than restrict capabilities. Browser isolation served as an important steppingstone, but the future belongs to comprehensive platforms that enable confident operation in any digital environment.
Replica transforms how organizations approach high stakes work by eliminating the traditional compromise between security and capability. Teams can now conduct the most sensitive activities with complete protection while maintaining the speed and agility that modern operations demand.
Ready to see how Replica compares to your current browser isolation solution? Contact us for a personalized demonstration of complete environment protection.
At Replica, we’ve always believed security isn’t just about technology—it’s about people. Behind every critical investigation, every malware analysis, every fraud disruption, there are dedicated professionals putting their expertise on the line to protect others.
Too often, their work happens in the shadows. It’s anonymous by necessity, yet indispensable to the safety and resilience of organizations, communities, and entire nations. That’s why we launched Replica Legends: a new space to highlight the extraordinary individuals and teams advancing the frontlines of security, research, and innovation.
Why Legends?
For over 20 years, our founders worked in cyber counterintelligence. They saw firsthand how exposure—even a single slip—could unravel years of investigations and put lives at risk. That perspective shapes everything we build at Replica: secure isolated environments that let professionals do their most sensitive work without fear of compromise.
But we also recognize that tools alone don’t win the day. It’s the analysts who map dark-web markets, the fraud investigators who trace scams across borders, and the developers who secure software supply chains who embody the resilience and ingenuity of this industry.
Replica Legends exists to celebrate them.
Stories That Inspire
Through this series, we’ll share profiles, stories, and conversations with the people who are redefining what’s possible in high-risk, high-stakes domains:
Each Legend represents the very best of what secure, mission-driven work can achieve when enabled by the right protections.
Building a Culture of Protection and Progress
Replica was founded with a simple but powerful belief: security should accelerate innovation, not hold it back. By shining a light on these Legends, we want to reinforce that mission and inspire others to continue advancing in their fields.
We also hope these stories spark conversation. Security leaders today aren’t just risk managers—they’re enablers of business velocity, charged with balancing innovation and protection in a landscape that changes daily. Replica Legends is our way of spotlighting the people showing us how it’s done.
Join Us
We invite you to explore the first Legends profiles at replicacyber.com/legends. And if you know someone whose story deserves to be told—whether they’re an analyst, investigator, developer, or innovator—reach out.
Because while Replica builds the secure isolated environments that make their work possible, it’s the people who make the impact.
06/09/2025
In cybersecurity, terminology can blur critical differences. “Virtual environments,” “secure desktops,” and “managed access” may sound similar, but the underlying architectures, and the risks they address, are profoundly different.
When mission-critical operations depend on trust, speed, and zero exposure, not all environments are created equal.
Not All Virtual Environments Are Truly Isolated
Some platforms offer cloud-based desktops intended for persistent use. These systems are often built on traditional VDI (Virtual Desktop Infrastructure) or browser isolation models, using shared hypervisors, persistent instances, and Remote Desktop Protocols (RDP) or Virtual Network Computing (VNC) for access.
While effective for basic workflows or identity abstraction, these models introduce significant security tradeoffs:
Regardless of whether you choose RDP or VNC, the following security best practices are crucial:
By understanding these security tradeoffs and implementing robust security measures, you can significantly reduce the risks associated with using both RDP and VNC for remote access
Replica takes a fundamentally different approach.
Replica’s Zero-Trust Isolation Model
Replica environments are built with true zero-trust principles from the ground up:
This isn’t just virtualization, it’s operational containment at scale.
Built to Scale with the Mission, Not the Machine
We’ve seen confusion arise when traditional desktop pricing models are used as a reference for secure environments. But Replica isn’t a desktop, it’s an execution layer built for comprehensive, high-intensity workflows that enable safe and contained collaboration.
Whether you’re:
Replica scales up or down instantly, without pre-allocated desktops or per-user licensing burdens. You only pay for what you use, when you use it.
Security That Empowers, Not Encumbers
Replica is purpose-built for:
With full observability, audit logs, and integration with SIEMs, proxies, and compliance tools, you don’t sacrifice visibility for protection, you gain both.
The Bottom Line
If your security needs go beyond identity management and into operational execution—Replica gives you the tools to operate confidently, without exposure. Not all environments are built for risk. Ours are.
See it in action. Get in touch →
In cybersecurity, terminology can blur critical differences. “Virtual environments,” “secure desktops,” and “managed access” may sound similar, but the underlying...
05/09/2025

MCLEAN, VA | August 5, 2025 — Replica Cyber, a leader in Zero-Trust Isolated Environments, today announced a major evolution of its flagship Replica platform that transforms how organizations accelerate high-stakes business operations. Building off its patented zero-trust environments which anonymize the attack surface, Replica now delivers instant, isolated workspaces for critical activities beyond security— from AI experimentation, isolated data sharing, full lifecycle M&A, secure engineering and development, threat operations and more—with unprecedented speed and protection. New features include mobile phone access, integrated business tools, and secure external collaboration capabilities. Unveiled during Black Hat USA 2025, the evolved platform addresses the core challenge facing modern enterprises: accelerating innovation and strategic operations without increasing security risk.
“Advantage in business or government is always a balance between risk and innovation,” said Kristopher Schroeder, CEO of Replica Cyber. “In working with our customers, we found that while Replica solves tough security challenges, it also unlocks broader business value. Whether integrating newly acquired tech, experimenting with next-gen AI, or disrupting emerging threats, the platform lets teams operate with confidence—without exposing networks, data, or intent. Once deployed, customers can pursue opportunities that were previously too risky.”
In this release, Replica introduces revolutionary secure file sharing through protected environments. These virtual environments enable collaboration with any external party—even non-Replica users, while allowing the owner to maintain control of their data. This breakthrough eliminates risky email exchanges and document sharing, opening secure collaboration possibilities that were previously impossible.
Built to solve critical cyber issues in national security, Replica is trusted by Fortune 100 companies and government agencies alike. The platform delivers transformative capabilities across three critical impact areas:
Partnerships to Increase Value for our Customers
Replica also launched the Replica partner program, a growing ecosystem that delivers best-in-class tools directly into secure environments. The program brings trusted solutions for secure development, threat intelligence, fraud detection, investigations, and more into isolated workspaces. At launch, Replica has partnered with ShadowDragon, Analyst1, SentinelOne, and Intel 471 with dozens of other tools previously deployed or available in Replica. The open architecture has always been designed to support future integrations as organizational missions evolve, and the Replica team will continue to pursue new partnerships that increase the value of the platform to our customers.
“Working inside the Replica platform gives our users protection when navigating sensitive and high-risk digital territory, allowing them to safely collect intelligence and conduct investigations while maintaining operational security and evidence integrity,” said Paul DiBello, SVP of Partnerships at ShadowDragon.
The Replica platform scales from small teams to enterprise-wide deployments and is available immediately as SaaS-delivered or private cloud, with flexible deployment options (including on-prem) to meet diverse organizational requirements.
The Replica team will be offering live demos and 1:1 meetings during Black Hat USA, August 2-7 in Las Vegas. For a custom demo, visit www.replicacyber.com/request-a-demo/ or learn about partnership opportunities at: www.replicacyber.com/become-a-replica-cyber-partner/.
About Replica Cyber
Replica Cyber delivers Zero-Trust Isolated Environments to global financial institutions, government agencies, and Fortune 100 companies. Founded by experts in cyber counterintelligence and mission-critical operations, the company holds 20 issued patents, delivering an anonymous attack surface for any work within the platform. As North America’s first B Corp-certified cybersecurity platform provider, Replica enables organizations to operate without detection, with full control and without compromise across the high-stakes digital missions that matter most.
About ShadowDragon
ShadowDragon provides comprehensive, cyber investigative resources and training for use by private companies, intelligence gathering professionals, law enforcement, and government. The U.S.-based company delivers open-source intelligence (OSINT) from over 500 networks including social media platforms, chat rooms, forums, historical datasets, and the dark web. The company monitors malware history, data breach dumps, and other areas for active cyber threats. These data collection and analytic tools help defend against malicious acts in the digital and physical world. For more information, visit the ShadowDragon Trust Center for details about the company’s approach to “OSINT for good.”
About Analyst1
Analyst1 is a premier cybersecurity solutions provider specializing in advanced threat intelligence. Founded by industry experts, the company’s cutting-edge Threat Intelligence Platform (TIP) leverages AI and machine learning to transform raw data into actionable insights. Trusted by government and commercial clients, Analyst1 empowers security teams to detect, assess, and respond to cyber threats efficiently. Headquartered in Reston, Virginia, Analyst1 continues to innovate, helping organizations stay ahead of evolving cyber risks. For more information, visit analyst1.com.
About SentinelOne
SentinelOne is a leading AI-powered cybersecurity platform. Built on the first unified Security Data Lake, SentinelOne empowers the world to run securely by creating intelligent, data-driven systems that think for themselves, stay ahead of complexity and risk, and evolve on their own. Leading organizations—including Fortune 10, Fortune 500, and Global 2000 companies, as well as prominent governments— trust SentinelOne to Secure Tomorrow™. Learn more at www.sentinelone.com.
About Intel 471
Intel 471 equips enterprises and government agencies with intelligence-driven security offerings powered by real-time insights into cyber adversaries, threat patterns, and potential attacks relevant to their operations. By integrating human-sourced intelligence with advanced automation and curation, the company’s platform enhances security measures and enables teams to bolster their security posture by prioritizing controls and detections based on real-time cyber threats. Organizations are empowered to neutralize and mitigate digital risks across dozens of use cases across our solution portfolios: Cyber Threat Exposure, Cyber Threat Intelligence, and Cyber Threat Hunting. Learn more at www.intel471.com.
MCLEAN, VA | August 5, 2025 — Replica Cyber, a leader in Zero-Trust Isolated Environments, today announced a major evolution...